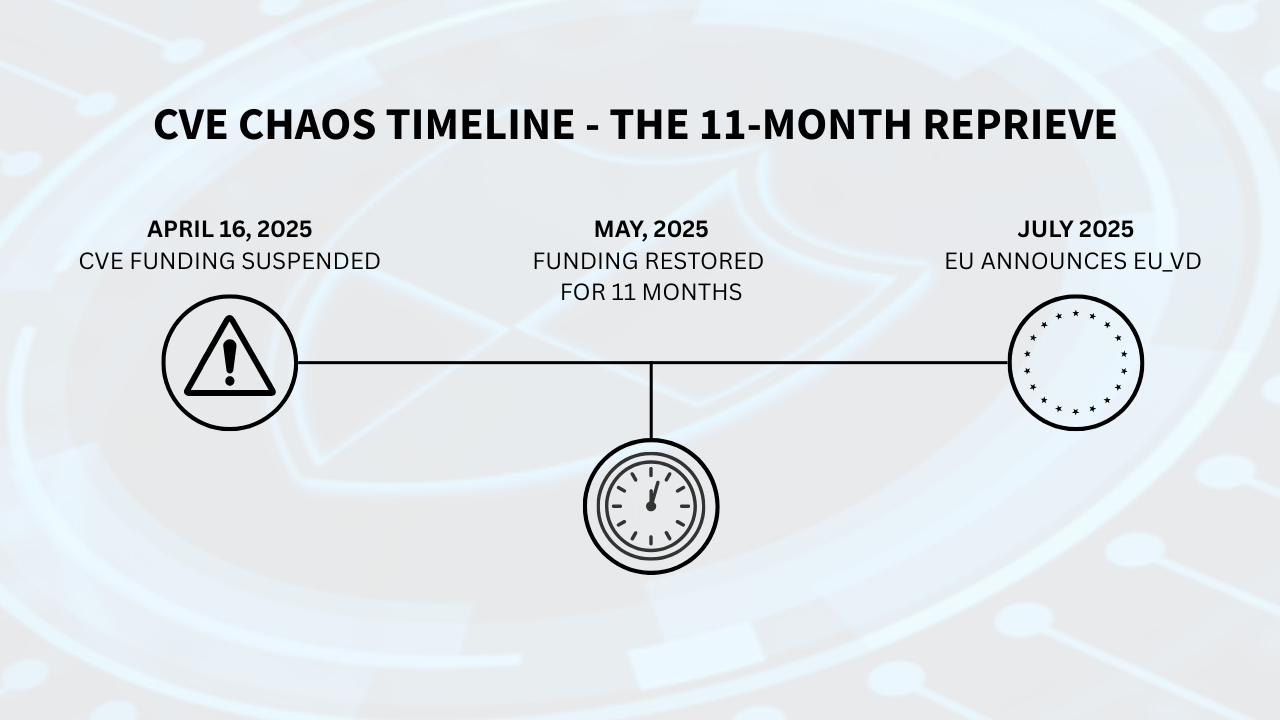
On Wednesday, April 16, funding for MITRE’s work on the Common Vulnerabilities and Exposures (CVE) Program — the global standard for identifying software security flaws — was set to expire. This news, confirmed by Yosry Barsoum, a MITRE Vice President, in a letter to the CVE board, sent shockwaves through the cybersecurity community.
Why Is the CVE Program So Important?
The CVE Program, managed by MITRE, provides unique identifiers (CVE IDs) for publicly reported cybersecurity vulnerabilities in software and hardware. Think of these as the “serial numbers” for digital flaws—the universal language that security tools, vendors, governments, and enterprises use to communicate about specific vulnerabilities.
Without this “master list,” organizations struggle to:
-
Track which vulnerabilities exist in their systems.
-
Share information across different security tools and agencies.
-
Coordinate responses across the entire cybersecurity community.
How Is the System Connected?
The NIST National Vulnerability Database (NVD) is a US government project that takes these CVE records and adds extra details:
-
CVSS Scores – They rate how dangerous a vulnerability is.
-
Platform Mappings (CPE) – They specify which software or devices are affected.
-
Impact & Remediation Guidance – They offer advice for fixing or mitigating the issue.
So, if the CVE list stops, the NVD — and all tools depending on it — cannot function. The analogy is like removing IBAN numbers from banking: it doesn’t just slow things down, it threatens the entire system’s reliability.
An Industry Shock, a Temporary Fix
When the possibility of the CVE program halting became public, the cybersecurity industry reacted immediately. Within weeks, the US government restored MITRE’s funding—but only for 11 months. This short-term patch revealed a deeper problem: the entire world relies on one organization, in one country, to maintain its most important cybersecurity “address book.”
Europe Responds—and a New Fragmentation Begins
Recognizing the risk in being dependent on a single US-managed authority, the European Union promptly announced its own project: the EU Vulnerability Database (EU_VD). This aims to serve both as backup and, potentially, as a long-awaited competitor to the US-dominated CVE system.
Why Does This Matter to Enterprises and Security Teams?
What used to be a single, authoritative database may now become many. Security teams will soon face:
-
Multiple vulnerability lists, each possibly using different formats and standards.
-
The need for tools and platforms to cross-check several sources.
-
Added costs, operational headaches, and the risk of getting inconsistent or delayed information.
At the heart of it: global coordination for vulnerability tracking has been destabilized.
The Core Problem — And the Path Forward
Repeated funding scares and geopolitical changes have proven that depending on a single source for critical risk data is unsustainable. Security leaders now face a pressing question: how do you navigate a fractured landscape?
Organizations must:
-
Prepare for a world with multiple, possibly conflicting, vulnerability databases.
-
Invest in Vulnerability Risk Management (VRM) systems that can pull from many sources, sort the signal from the noise, and translate raw CVE data into business-relevant risk intelligence.
Action Items:
-
Are your security and risk teams prepared for a fragmented vulnerability landscape?
-
Do you have a plan to merge and analyze threat information from multiple databases?
-
Or are you still hoping that “someone else” will keep the master list—and your security—intact?
In today’s world, a bureaucratic decision can disrupt cybersecurity everywhere. It’s time to move from outsourcing risk intelligence to building distributed, business-contextualized solutions internally.
If you’re relying on a single vulnerability feed, now’s the time to rethink—not just your technology, but your entire approach to risk governance.
Key Takeaway:
The global cybersecurity system is only as strong as its foundations. With the CVE funding scare, those foundations were rattled—ushering in an era where organizations must actively manage their own risk intelligence, rather than betting on a single, centralized source.