Often times we use terms like exploits , threats and vulnerabilities interchangeably. But, are they the same, or even similar ? Not really. It’s important to understand the differences so that we deal with them appropriately.
- Threat: A potential danger that can target weaknesses in a system.
- Vulnerability: A flaw or weakness that can be exploited by a threat.
- Exploit: The method or tool used to take advantage of a vulnerability.
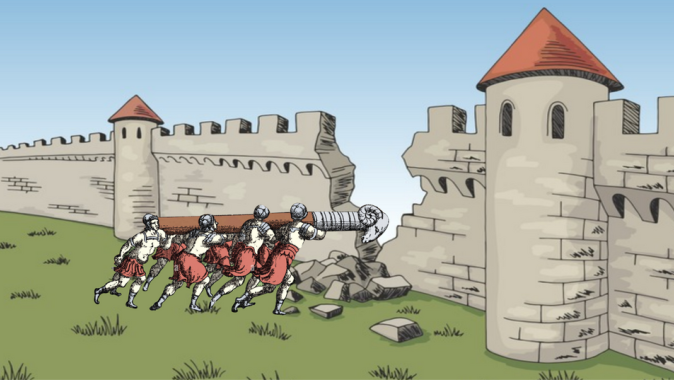
- Threat: Enemy forces planning an attack.
- Vulnerability: A crack in the fort’s wall.
- Exploit: A battering ram used to breach the weak wall.
If the crack (vulnerability) did not exist, the enemy (threat) would have no easy way in, and the battering ram (exploit) would be useless.

Three Real-World Threats and How They Were Exploited
1. SQL Injection Vulnerability in Web Applications
- Event: 2019 SQL Injection Attack on Microsoft Customer Support Database
- Threat: Attackers seeking unauthorized access to sensitive customer records.
- Vulnerability: Unpatched SQL injection flaw in Microsoft’s support database.
- Exploit: Attackers injected malicious SQL queries to extract confidential data.
2. Unpatched Windows Vulnerability (EternalBlue – SMBv1 Flaw)
- Event: WannaCry Ransomware Attack (2017)
- Threat: Cybercriminals deploying ransomware.
- Vulnerability: Unpatched SMB protocol flaw in Windows.
- Exploit: Attackers used the EternalBlue exploit (developed by the NSA and later leaked by Shadow Brokers) to spread malware across networks.
- Impact: Over 230,000 systems in 150+ countries were infected, causing billions in damages.
Remote Code Execution (RCE) Vulnerability in Log4j (Log4Shell – CVE-2021-44228)
- Event: Log4Shell Exploit (2021)
- Threat: Cybercriminals exploiting open-source logging frameworks.
- Vulnerability: A flaw in Apache Log4j allowed arbitrary remote code execution.
- Exploit: Attackers sent specially crafted log requests to gain control over vulnerable systems.
- Impact: Millions of servers globally were affected, impacting companies like Amazon, Microsoft, and Cloudflare.
Case Study: Equifax Data Breach (2017) – How a Threat Exploited a Vulnerability
1. Background
Equifax, one of the largest credit reporting agencies, suffered a massive data breach in 2017, exposing the personal data of 147 million people, including Social Security numbers, birth dates, and addresses.
2. Threat
- Threat Actor: Cybercriminals seeking financial and identity data.
- Objective: Gain unauthorized access to Equifax’s sensitive databases.
3. Vulnerability
- Flaw: Unpatched vulnerability in Apache Struts (CVE-2017-5638), a widely used open-source web framework.
- Weakness: A remote code execution (RCE) vulnerability allowed attackers to run arbitrary code on Equifax’s servers.
- Risk: The flaw, if exploited, could give attackers full control over the system.
4. Exploit
- Method: Attackers used an automated exploit to send malicious requests to Equifax’s web application.
- Impact: Hackers remained undetected for 76 days, extracting sensitive data.
5. Consequences
- Data Stolen: 147 million customer records, including SSNs, birth dates, and addresses.
- Financial Impact: Equifax paid $700 million in settlements and fines.
- Regulatory Fallout: The company faced lawsuits, reputational damage,
and stricter compliance requirements.
6. Lessons Learned & Prevention
- How This Could Have Been Prevented:
- Patch Management: The vulnerability had a patch released in March 2017, but Equifax failed to apply it before the attack in May 2017.
- Threat Monitoring: Security teams should have detected unauthorized access earlier.
- Network Segmentation: Sensitive data should have been better isolated to limit exposure.
Three Notable SQL Injection Exploits
1. Yahoo SQL Injection Attack (2014)
- Exploit: Hackers used an automated SQL injection script to extract usernames and passwords from Yahoo’s database.
- Impact: Millions of user credentials were compromised, increasing the risk of credential-stuffing attacks.
2. TalkTalk Data Breach (2015)
- Exploit: Attackers exploited a weak SQL vulnerability in TalkTalk’s website to inject malicious queries and extract over 150,000 customer records,
including bank details and personal information. - Impact: The breach cost TalkTalk £60 million in damages and led to a £400,000 fine from the UK Information Commissioner’s Office (ICO).
3. Heartland Payment Systems Breach (2008)
- Exploit: Cybercriminals used an SQL injection attack to compromise Heartland’s payment processing system, injecting malicious SQL queries to gain access to financial transactions.
- Impact: 134 million credit card transactions were compromised, making it one of the largest payment card breaches in history. The company paid $145 million in settlements and compliance costs.
A threat represents the possibility of an attack occurring, while a vulnerability is a weakness that can be exploited. Exploits are the methods attackers use to leverage these vulnerabilities. Understanding this relationship is critical for organisations to protect themselves by identifying vulnerabilities and implementing robust security measures.